
An incomplete security patch by NVIDIA has left the critical vulnerability CVE-2024-0132 unresolved—posing serious risks to containerized environments that rely on the NVIDIA Container Toolkit. Despite efforts to fix the flaw, security researchers have found that the underlying issue persists, opening the door to potential container escapes and system compromise. This blog breaks down the vulnerability, the failed patch, and what teams can do to protect their infrastructure.
Background of CVE-2024-0132
Initial Discovery and Reporting
CVE-2024-0132 is a serious vulnerability discovered in NVIDIA’s Container Toolkit, a critical tool for running GPU-accelerated workloads in containerized environments. The flaw was initially identified by security researchers who found that improper handling of symbolic links could allow attackers to execute unauthorized code outside the intended container boundaries.
NVIDIA’s Initial Response and Patch
NVIDIA responded by releasing a patch aimed at fixing the issue. However, while the patch addressed some aspects of the vulnerability, it failed to completely mitigate the underlying problem—leaving systems still exposed to potential container escapes.
Analysis of the Incomplete Patch
Findings from Trend Micro’s Research
According to a detailed analysis by Trend Micro, the patch did not fully neutralize the symbolic link vulnerability. The incomplete fix allowed attackers to exploit certain edge cases, especially in environments with lax container runtime configurations.
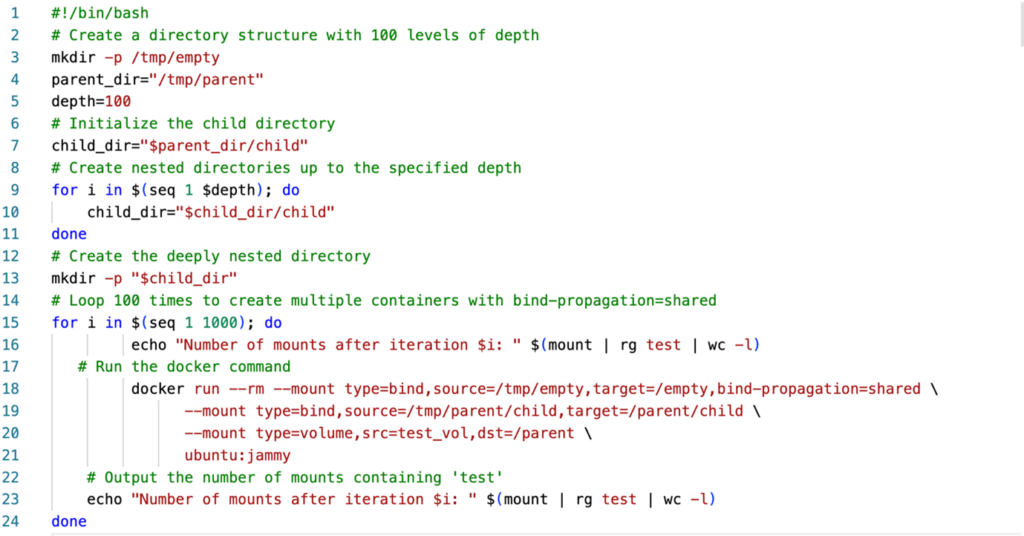
Implications of the Incomplete Fix
The main issue lies in how container file systems handle symbolic links and mount points. In certain configurations, attackers can still perform write operations on the host system, potentially leading to privilege escalation or full container escape.
Potential Risks and Impact
Container Escape Vulnerabilities
CVE-2024-0132 poses a significant threat to container security. Successful exploitation means that a malicious actor operating within a container could escape its boundaries and access the host system—violating one of the core principles of container isolation.
Denial-of-Service (DoS) Concerns
Beyond privilege escalation, the flaw can also be weaponized for Denial-of-Service (DoS) attacks. Malicious containers could disrupt host resources, leading to service outages or degraded performance, especially in GPU-dependent environments like AI training clusters.
Mitigation Strategies and Recommendations
Apply the Latest NVIDIA Toolkit Patch
Start by applying the latest available update. While this does not completely resolve the issue in all configurations, it addresses part of the vulnerability and is a necessary first step.
Image suggestion: Screenshot of the NVIDIA download/update page with the latest version highlighted.
Implement Defense-in-Depth Controls
Security professionals should apply layered defenses to reduce exposure:
- Avoid Privileged Containers: Do not run containers with
--privilegedmode, and limit capabilities using--cap-drop=ALLand selectively--cap-addas needed. - Constrain Filesystem Access: Avoid unnecessary host directory mounts and use read-only file systems where possible. Monitor symbolic link creation inside containers.
- Apply Runtime Security Policies: Use AppArmor, SELinux, or seccomp to restrict the actions a container can perform. These tools can block unauthorized file operations or system calls.
- Monitor for Anomalies: Employ runtime security tools like Falco or container-aware monitoring systems to detect suspicious behavior.
Conclusion
CVE-2024-0132 highlights the complexity of container security and the risks of incomplete patches. Even industry giants like NVIDIA can miss critical scenarios when responding to vulnerabilities. Organizations must remain vigilant, not only by applying vendor patches promptly but also by layering defenses and monitoring continuously.
